HP Anyware Security¶
HP Anyware incorporates features that maximize the security of any deployment model, including on-premises, hybrid or public cloud architectures:
- RADIUS-based multi-factor authentication (MFA).
- All PCoIP components use security certificates to ensure a trusted, end-to-end Transport Layer Security (TLS) connection for TCP communications.
- The PCoIP UDP protocol is encrypted with industry-standard secure AES-256 encryption.
- HP Anyware Connector ensures secure PCoIP traffic flow between external and internal networks.
- The PCoIP protocol is host-rendered and no data ever leaves the remote workstation, except encrypted pixels.
Firewall Settings¶
The PCoIP protocol uses ports UDP:4172, TCP:4172 and either TCP:443 or TCP:60443 as preferred. These ports must be open to allow the flow of PCoIP traffic through the firewall. For an in-depth look at the port settings for different environments relating to HP Anyware, PCoIP Management Console and PCoIP Zero Clients, see the following KB Article.
Security Certificates¶
Certificates are used to ensure that all communication endpoints are trusted. All communications between PCoIP components are performed over encrypted secure channels that use certificates for validation.
MFA Integrations with Anyware Manager¶
It is possible to integrate third-party MFA applications with Anyware Manager and HP Anyware. We have tested MFA integrations with certain applications and versions of HP Anyware, within specific environments. The links outlined below point to knowledge base articles that outline the processes involved in setting up these specific integrations.
Third-Party MFA Information
The knowledge base articles contain steps and processes that were accurate at the time of testing. We do not take responsibility for updates to third-party applications, or updates to how these applications work. Using different versions of these applications may not yield the same results and may lead to different behavior. If you discover that the steps outlined below are no longer valid, please contact us and we will investigate.
Disaster Recovery¶
Business continuity can take many forms. Whether it be a bank processing transactions without interruptions, a retail store transacting sales at point of sale terminals, or universities running computer labs with zero downtime, business continuity is important to every type of organization. Downtime can result in significant losses in revenue or permanent damage to a brand's reputation.
HP Anyware is a perfect option and solution to base your companies and organizations disaster recovery plan around. For detailed information on ow to use HP Anyware as part of your disaster recovery strategy, see Disaster Recovery for Virtual Desktops.
Corporate Security Compliance¶
Isolating a Secure Content Network¶
Major media and entertainment corporations rely on the PCoIP protocol to conform with MPAA (Motion Picture Association of America) and CDSA (Content Delivery and Security Association) best practices in addition to meeting Trusted Partner Network (TPN) compliance obligations. Media assets are securely isolated on production networks, only accessible from authorized network endpoints as an AES-256 encrypted stream of pixels. As media assets themselves are never downloaded to the endpoints, intellectual property remains secured, no matter what applications are used, as outlined in the image below.
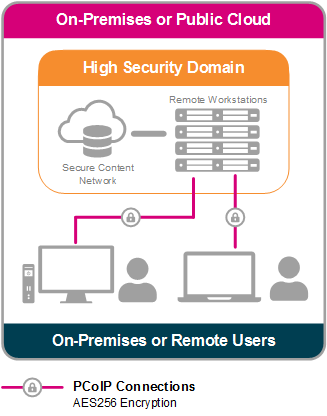
Accessing the Public Internet from an Isolated Workstation¶
Users inside highly secured enterprises, such as TPN certified environments or those compliant with MPAA or CDSA best practices, may require the public internet for access to media assets or other information. HP Anyware enables isolated remote workstations, such as those attached to content networks, to access the public internet via back-to-back PCoIP connections as outlined in the image below.
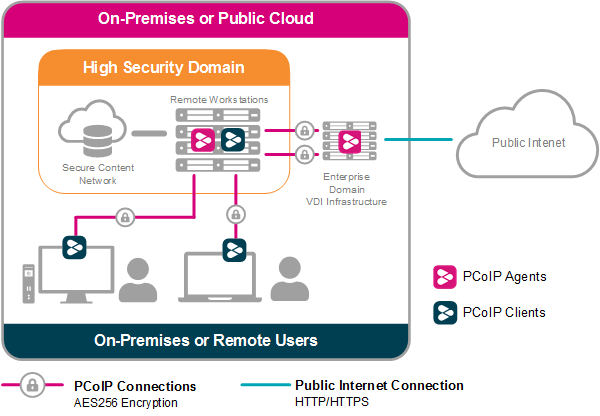
Referring to the diagram above, the secured remote workstation is deployed with both PCoIP Agent software and PCoIP Client software. While the PCoIP Agent software serves encrypted pixels to the user at the PCoIP Client, a second PCoIP Agent deployed on a generic virtual desktop outside the high security domain serves the remote workstation with the internet browser image of the virtual desktop, also in the form of encrypted pixels. Such an architecture, supported on Windows, macOS, and Linux remote workstations, ensures that the airgap perimeter of the high security domain is only traversed with encrypted pixels which adheres to compliance practices.d